AWS Cloud Foundation
Below is an approach and methodology to build Cloud Foundation in AWS securely
Benefits of AWS Cloud Foundation:
pre-requisite for Migration. It helps to deploy or migrate workloads securely. Accelerates Cloud Adoption. Set of Industry standards and best practices. Reduces re-work
Components of AWS Cloud Foundation:
Landing zone, Account and VPC topology, Account vending, Service catalog. Setting up Network connectivity between on-prem and AWS securely, Setting up DevOps, Security, Logging and monitoring tools. Enabling preventive and detective controls, Guardrails, automated Governance and compliance, FinOps. Identity and access management, Golden Images, Encryption, Certificate management, Policies and framework for Secured and automated Governance.
Landing zone:
- Secure pre-configured environment for AWS presence
- Scalable and flexible
- Enables Agility and Innovation
AWS Landing zone:
- Implementation of landing zone based on multi-account strategy guidance
AWS Control Tower:
- AWS Service version of AWS Landing Zone.
- AWS Control Tower automates the set-up of a baseline environment, or landing zone, that is a secure, well-architected multi-account AWS environment.
- Builds core account structure, establishes Account Factory, AWS Organizations, Configures preventive and detective controls
- Centralize Identity, access and logging. Automate compliant account provisioning.
Landing zone Accelerator on AWS:
- Integrates additional AWS security services, establishes foundational networking infrastructure, provides configuration management
- Accelerates the implementation of security controls on AWS
- Compliments control tower.
Control Tower vs Landing zone — Selection criteria:

Landing zone Accelerator Architecture:
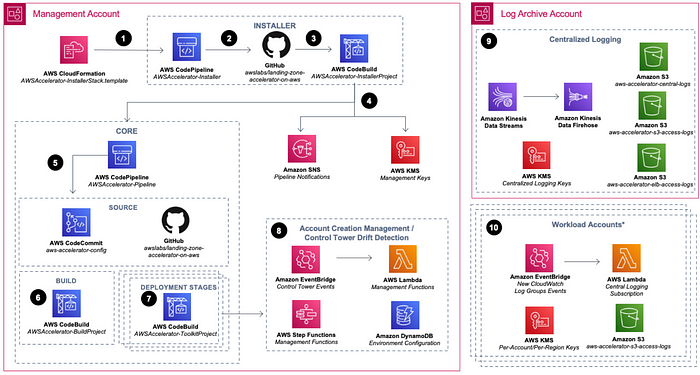
Landing zone accelerator Deployment approach:
- Use AWS CloudFormation to install the solution into your environment. It deploys a code pipeline.
2. The Installer pipeline (AWSAccelerator-InstallerStack) functions separately from the Corepipeline
3. An AWS CodeBuild project functions as an orchestration engine to build and run the solution’s AWS CDK application that deploys the Core pipeline (AWSAccelerator-PipelineStack) and its associated dependencies.
4. The solution deploys Amazon Simple Notification Service (Amazon SNS) topics that you can subscribe to for alerts on Core pipeline events. Additionally, the solution deploys two AWS Key Management Service (AWS KMS) customer-managed keys to manage encryption at rest of Installer and Core pipeline dependencies.
5. The Core pipeline validates and synthesizes inputs and deploys additional CloudFormation stacks with AWS CDK. An AWS CodeCommit repository named aws-accelerator-config stores the configuration files that the solution uses. These configuration files are the primary mechanism for configuring and managing the solution.
6. An AWS CodeBuild project compiles and validates the solution’s AWS CDK application configuration
7. Multiple AWS CodeBuild deployment stages deploy the resources that were defined in the solution configuration files to your multi-account environment.
8. The solution deploys resources that monitor AWS Control Tower lifecycle events to detect potential drift against a known good state. The solution also deploys resources that can automate the enrollment of new AWS accounts into your multi-account environment.
9. The solution deploys centralized logging resources in the Log Archive account in your multi-account environment.
10. You can enroll and provision workload accounts into your multi-account environment with additional infrastructure through the solution’s configuration files.
AWS Services used in Cloud Foundation:
Infra. Protection: AWS Network Firewall, AWS Firewall Manager, AWS Shield, AWS WAF (Web application Firewall), Amazon VPC, AWS Private link, AWS Systems Manager
Identity and Access Management: AWS IAM, AWS IAM Identity Center, AWS Organizations, AWS Directory Services, Amazon Cognito, AWS Resource Access Manager (RAM)
Detection: AWS Security Hub, Amazon GuardDuty, Amazon Inspector, Amazon CloudWatch, AWS Config, AWS CloudTrail, VPC Flow Logs, AWS IoT Device Defender
Data Protection: Amazon Macie, AWS KMS, AWS CloudHSM, AWS Certificate Manager (ACM), AWS Secrets Manager, AWS VPN, Server side encryption
Compliance: AWS Artifact, AWS Audit Manager
Incident response: Amazon Detective, AWS Elastic Disaster Recovery, AWS Config., AWS Lambda
Best practices in AWS Cloud Foundation:
- Automate account provisioning and customization ( AWS Service Catalog, AWS CloudFormation, AWS Control Tower)
- Enable visibility to track user activity and risk across your environment (use AWS Organization, AWS Config, AWS CloudTrail)
- Define controls using a policy-as-code model and enforce peer review (AWS Organization, AWS Config, AWS Control Tower)
- Align control objectives to a security framework (AWS Security Hub, AWS Config, AWS Control Tower)
- Use preventive controls to protect security baselines and proactive controls to stop security misconfigurations from being deployed (AWS Organization, AWS Config, AWS Control Tower)
- Continuously monitor and test control effectiveness (AWS Organization, AWS Config, AWS Audit Manager)
- Design an Org structure that is flexible for future requirements
- Use the ‘Data residency’ and ‘Regions deny’ controls for regulated environments
- OU should not reflect your business structure, instead should reflect your policy structure
- Use separate Sandbox OU for PoC
- Use Config rule for Detective controls (Detect resources that violate your defined security policies)
- Use CloudFormation Hook for Proactive controls (scan resources before they are provisioned, blocking provisioning of resources if they are not compliant)
- Enforce standards through controls and categorize into Mandatory, Strongly recommended and Elective controls
- Use AWS Control Tower Controls Library — 390 controls, 39 services, 3 frameworks (NIST, PCI DSS, CIS)
- Disallow deletion of log archive
- Disallow config changes to cloudTrail
- Use service control policies for preventive controls (disallow actions that would lead to violations of security policies)
- Harden AWS services and images
Cloud foundation design principles
- Apply security at all layers
- Enable traceability
- Implement a strong identity foundation
- Automate security best practices
- Protect data in transit and at rest
- Keep people away from data
- Prepare for security events
